Smart Grid Security and Defensive Military Architecture of the Middle- ages; an Interesting Comparison
Why are our castles now just romantic ruins?Part of the answer is gunpowder, and the eventual victory of the iron projectile over stone walls. But, a more fundamental reason is their static nature, their focus on layers of defensive perimeters and their inability to adapt to more agile and fluid forms of warfare.
In many respects, the battle against the cyber-attacker is similar, especially as it relates to the low-voltage smart grid.
Both vendors and utilities in the low-voltage smart grid industry have focused on multiple lines of defensive positions to secure their smart grid, using technology to create barriers. The underlying concept is that the more barriers you have, the better you can block an attack. If the attacking force was an ill-equipped and poorly educated rabble, led by a few unimaginative iron-clad knights, then that is probably enough.
However, the reality is that cyber-attackers may not be smarter than those we trust to protect us (CISOs, CTOs, CIOs, regulatory and certification bodies, governments), but they are typically far better motivated – either for financial gain, fame (or at least notoriety and personal kudos amongst peers), ideology (terrorism) or loyalty and national pride (fighting as a “soldier” for a nation state).
They will undertake reconnaissance missions to learn about defences, they will assess whether previous successful attacks will work on a new target, they will attack where they see a weakness, they will attack at multiple points in different ways simultaneously to confuse and overwhelm defences, and they will exploit the non-technological points in the defence; the humans, the process, the “old-stuff” and the “forgotten old-stuff”. They will get past the defences, given time and perseverance.
Thinking of the security of the smart grid in terms of multiple layers of slow-moving or static defensive measures is like applying a castle to modern war. Whilst protection is important, what is needed is a more agile approach incorporating the ideas of threat detection and response to initiate pre-planned reactions to protect key assets, identify the intruder, and limit the damage they can do. This is all based on the assumption that the protection will eventually be breached.
What changed to make us want to review our security strategy?
In short, complexity and sophistication in the low-voltage grid.
The cyber-attacker exploits the fact that a complex system will likely have loop-holes to gain access. Once inside, they can exploit the sophistication of the system to spread the damage that they can do as far and wide as possible, should they be motivated to do so.
As little as a few decades ago, all the complexity and sophistication of the grid was near the centre in the high and medium voltage grid, and all the security was there too. A cyber-attacker could do little or no damage from the low-voltage grid. With the introduction of smart meters and increased “smarts” in the sub-station and other nodes in the low-voltage grid, the complexity and sophistication are now in the low-voltage grid as well, all the way to the consumer and the privacy of their homes.
The massive increase in the attack surface, together with the opportunity to do malicious damage, means that the threat and the risk substantially escalated with the introduction of the smart grid. Especially, as all the things energy companies expect the smart grid to provide, also offers the cyber-attacker the means to do damage.
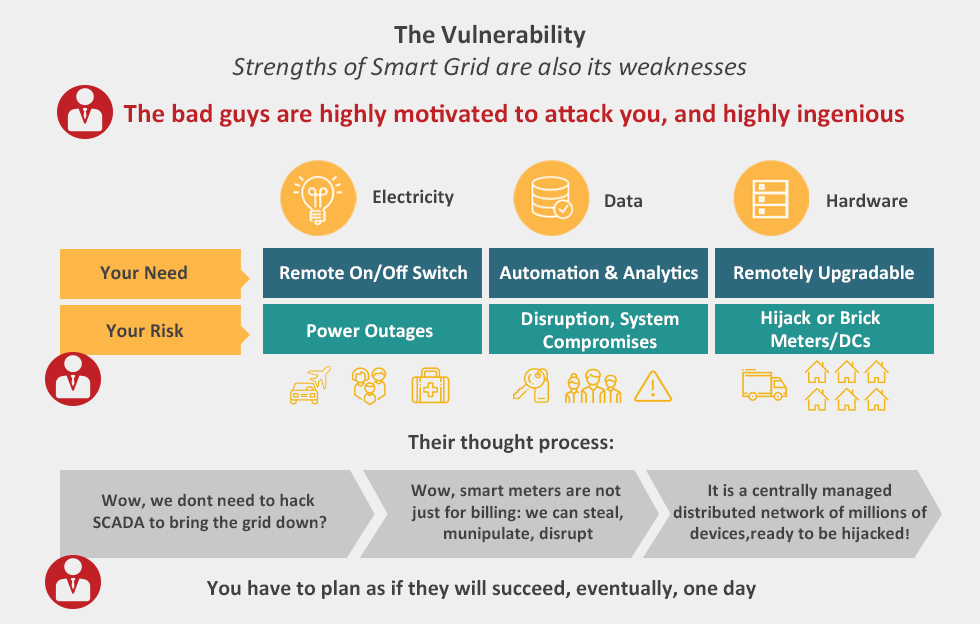
The Vulnerability
Strengths of Smart Grid are also its weaknesses
 The bad guys are highly motivated to attack you, and highly ingenious
The bad guys are highly motivated to attack you, and highly ingenious



Your Need
Your Risk
Remote On/Off Switch
Power Outages

Automation & Analytics
Disruption, System Compromises

Remotely Upgradable
Hijack or Brick Meters/DCs

We need to start looking more at the low-voltage grid
Of course, the focus on any defence is to protect the points where the most damage can be done if successfully attacked. The SCADA systems of the high and medium voltage grid have received the attention and budgets they deserve due to their asset value and centralised position in the supply of energy. The same focus needs to be applied to the low-voltage grids so that the latest ICT industry honed security practices are implemented in this domain because:
• Even if there are no records of attacks on the low-voltage grids that does not mean there are no attacks or intelligence gathering activities
•The cost of implementing traditional protection mechanisms or regulatory compliance-based security features in the low-voltage grid need not be a major blocker with the introduction of advanced threat detection solutions.
The result has been to develop a semi-static position, just like a castle, where the focus is on building protection mechanisms. Whilst not quite “set in stone” like in the castle, the cost and effort required to adapt existing defences to face new threats can be prohibitive.
The important point is to recognise a threat, a change in the level of threat, or whether an attack is taking place. Without evidence of threat or attack, the only option is to make assumptions: either there is no threat or attack (the optimistic view), or the information gathering attacks being mounted by cyber-attackers are completely successful, and the potential victims are unaware they are taking place.
The Focus on SCADA Systems
Protect the biggest assets in a central position

 Generation
Generation  Transmission
Transmission  Distribution
Distribution 
 Customer
Customer Driving a defense based on perimeter protection
No publicly known successful cyberattacks to date via the low-voltage grid
- Has not been the focus for the defender
- Attackers need time to develop expertise and tools
Business cases assume device lifespan of 10 - 20 years
- Today's cyber-security requirements were not anticipated with the first smart grid deployments and will change dramatically in the lifespan of today's deployments
Fast-paced adoption to meet EU 2020 Directive
- Prioritizing increased efficiency and new business opportunities over potential bad actors
Security fixes can be time consuming and costly to apply to old infrastructure
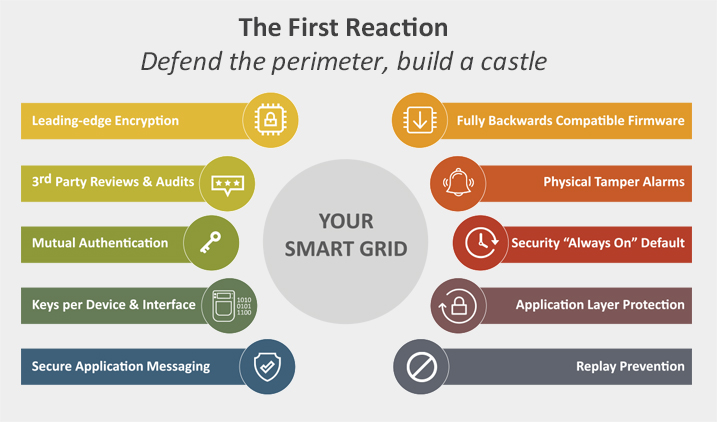
Defend the Perimeter
Build a castle with concentric lines of defence
Leading-edge Encryption

Fully backwards Compatible Firmware

3rd Party Reviews & Audits

Physical Tamper Alarms

Mutual Authentication

Security "Always on" Default

Keys Per Device & Interface

Application Layer Protection

Secure Application Messaging

Replay Prevention

YOUR
SMART GRID

Will protection mechanisms make me secure?
Of course, investing in protection mechanisms is entirely appropriate and necessary, and the more security aware smart grid solutions employ multiple lines of defence that cover all anticipated mechanisms of attack. They make it as hard as is technologically possible for the cyber-attacker to get past them.
What is wrong is the suggestion that having built protection mechanisms, you are protected.
Experience from the ICT industry has taught us that the cyber-attacker will find a way to exploit humans, processes, “old stuff” and “forgotten old stuff” to by-pass or subvert more up-to-date defences. Building defences requires that you know the form of attack, and we should assume that the cyber-attacker will be more ingenious than the defenders and might develop an attack from unanticipated directions.
Will regulatory standards make me secure?
Several countries and international bodies are implementing stringent new security practices which the equipment vendor is responsible for complying with. Of course, these help as they establish a minimum set of defences and should be applied where possible even if not mandated.
However, certifications are public and help the cyber-attacker in two ways:
•They will know what to expect and may have attack methods from other industries that they know to have been successful against similar or identical forms of defence.
•They will know what to avoid, and so they do not waste time on the harder defences, and look instead for the gaps.
The cyber-attackers are agile and will quickly establish and then possibly publicise potential or actual weaknesses.
Reliance purely on certifications may also lead to other deficiencies:
• Certifications are “point in time”; whilst cyber-security should be a process of continuous assessment and improvement. Furthermore, there is a risk that cyber-security budgets are consumed on compliance, and so starve the on-going and continuous nature of cyber-security of funds
Compliance Helps Set Minimum Protection
Examples of leading initiatives
Switzerland (METAS) is now requiring that all new smart meter solutions pass a penetration test before they can be sold/deployed in the country

Oesterreichs Energie defined a security requirements catalog that became the defacto requirements for all new smart meter projects in Austria. Includes role-based security, firmware separation and key management

ESMIG Defined a set of minimum security requirements under ETS/IEC with the goal of using them for security certification in Europe.
The goal of these is to agree on security requirements and enforce smart meter vendors (not utilities) compliance. These focus on preventative controls,not detection and response.
• Certifications provide for a generalised defence; whilst a defence against cyber-attackers should be tailored towards the specifics of the enterprise and an assessment of types of attack it will be subjected to.
Finally, these certifications still focus on the protection, and so do not address the inevitable outcome of a successful penetration and the resulting need for detection and response.
So, following the regulation, even where not mandatory, provides protection that might otherwise be missing. But, it does not replace the need for an active and evolving cyber-security strategy for the low-voltage grid, specific to the local threats.
Compliance Hepls Set Minimum Protection
Examples of leading initiatives
Switzerland (METAS) is now requiring that all new smart meter solutions pass a penetration test before they can be sold/deployed in the country

Oesterreichs Energie defined a security requirements catalog that became the defacto requirements for all new smart meter projects in Austria. Includes role-based security, firmware separation and key management

ESMIG Defined a set of minimum security requirements under ETS/IEC with the goal of using them for security certification in Europe.
The goal of these is to agree on security requirements and enforce smart meter vendors (not utilities) compliance. These focus on preventative controls,not detection and response.
How to improve the security of our castle
So, we have built a castle using all the perimeter defences that we can. We have used as much technology as is practical, limited by the cost, available time, infrastructure age and other limiting factors.
Let’s start by assuming that the perimeter is not perfect – the castle walls may have loop-holes that can’t be blocked or that we don’t even know about and the locks are too expensive to replace in this year’s budget. OK, so let’s start by putting cheap trip-wires outside the castle so that we know about reconnaissance and preparatory activity beyond our walls and can be prepared for an attack. That way, we know about the threat and can sensibly respond to a change in underlying threat level.
Let’s now develop ways that we can see the attackers in more detail from the trip-wires they hit, learn something of their intentions, assess the threat they pose and even identify who they are. This way, we know if this is a reconnaissance expedition or a major attack, and can then respond accordingly.
Let’s now assume that someone can get in and so there is a need to put trip-wires within the castle walls. Maybe, we put more where we think we are weak, but we also put some where we believe ourselves to be stronger just in case we are wrong.
Finally, let’s develop mechanisms to limit the damage that can be done; trap-doors that slam shut to limit the access the attacker has to more vulnerable parts. Sure, that might make life harder for the defenders in the short-term (as some of their flexibility may be limited), but it is far worse for the attacker, as their means of exploitation has been blocked.

Can you see them?
How to improve the security of our smart grid
Let’s apply the castle situation to the smart grid and see where this takes us. The key is to know the threat level and identify, preparations for attack, actual attacks and successful penetrations of the protection we have put in place.
In effect, the trip-wires are intelligent use of information to identify security related events. Some of these features will be available in many smart meters, but the full set of trip-wires will only be available from those smart meters that have focused on security and have credentials to prove it. In fact, many of the trip-wires are available from the investments made in protection mechanisms, so we are really leveraging that investment, but in a more organised way.
Once the trip-wires are working, there needs to be a conceptual shift from identifying and tracking individual security events to gaining an evolving appreciation of security incidents. By looking at a security incident, over a time-line, we have developed a method that makes it is possible to identify the level of threat, changes in that threat, the nature of the attack, and put in place defence mechanisms to limit the damage that can be caused.
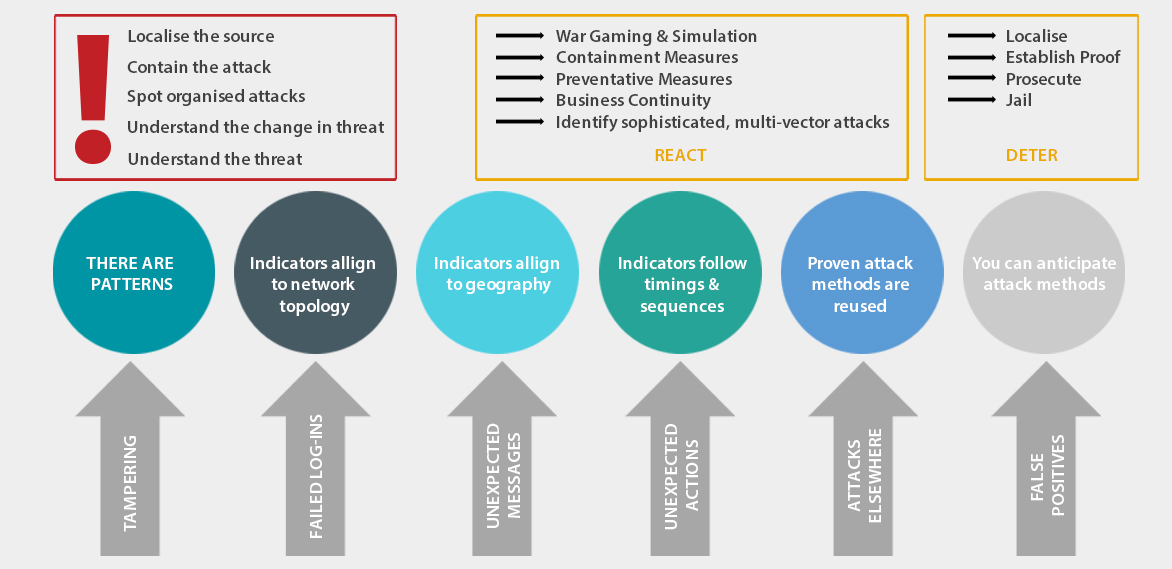

Localise the source
Contain the attack
Spot organised attacks
Understand the change in threat
Understand the threat

War Gaming & Simulation

Containment Measures

Preventative Measures

Business Continuity

Identify sophisticated, multi-vector attacks
REACT

Localise

Establish Proof

Prosecute

Jail
DETER
The industry perspective
A short survey illustrates the growing importance of detection strategies for the low-voltage grid:
 DisagreeAgree
DisagreeAgreeDetection solutions focused on the low-voltage grid are becoming more important. These allow energy suppliers to recognise whether a lack of cyber-criminal activity on the low-voltage grid is real or simply that information gathering attacks are going unnoticed
 DisagreeAgree
DisagreeAgreeAnticipation of specific attacks helps in the creation of detection strategies. Work is clearly taking place in this area, but can be accelerated so that energy suppliers can anticipate a wider range of attacks and use these as part of the mechanism for development of detection strategies
 DisagreeAgree
DisagreeAgreeWhilst the ability to detect a information gathering attack is developing, with a large attack surface, such as the low-voltage grid, it is important to have detection that is sensitive to abnormal behaviour which is indicative of threats and attacks that might not have been anticipated
 DisagreeAgree
DisagreeAgreeResponse is the next step after detection and relies on detection. As part of a detection strategy, it is important to define how a detected threat or breach will be responded to. It is important to avoid making that decision in a time of crisis - it is better to prepare in advance
 DisagreeAgree
DisagreeAgreeWith the mass of potential indicators of threat, information gathering and actual attack from the low-voltage grid, systems are critically important to help recognise and highlight distinct cyber-security incidents. Systematic detection helps energy suppliers to recognise cyber-criminal activity
 DisagreeAgree
DisagreeAgreePre-planning for responses to attack from the low-voltage grid is important and comes after anticipation of types of attack and putting in place mechanisms to detect these, and other indicators of abnormal activity. Doing this in crisis mode during an attack is not effective - instead, energy providers need to develop pre-planned responses and test these out in simulated scenarios. Red-team/Blue-team approaches to testing protection, detection and response are an important part of this
 DisagreeAgree
DisagreeAgreeWith its wide attack surface, the low-voltage grid is becoming more of a point of concern for energy suppliers. With such a varied and heterogeneous set of infrastructures deployed, it is hard to establish a consistent set of protection mechanisms, and so breach must be assumed. In which case, threat detection, driving response, is an important part of an integrated cyber-security strategy for the low-voltage grid
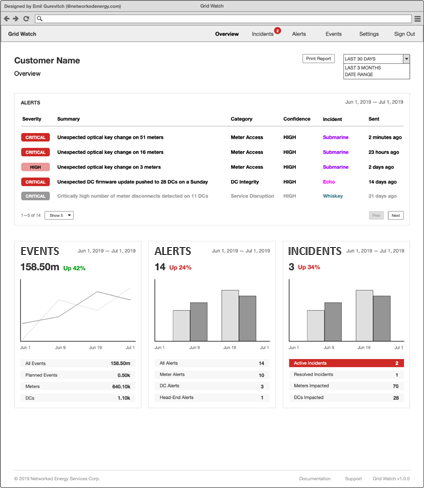
A practical solution – Protect, Detect and Respond
NES Grid Watch provides advanced analytics and threat detection that have been developed for specific low-voltage smart grid security threats and attacks. This identifies specific types of security incidents, which may indicate cyber-attacker reconnaissance, preparations for attacks, actual attacks, and successful penetrations. These capabilities are deployed out-of-the-box and immediately available – there is no need to enter a major development programme to create these analytics capabilities.
Through Grid Watch, you obtain visibility of the activities of cyber-attackers, for multiple attack scenarios including:
• Denial of service, power outages
• Derailment of operational and business algorithms, Billing, Operations
• Ransom, of customer information, of corporate information, of assets and of service.
NES Grid Watch sits “on-top” of your smart grid infrastructure, monitoring incidents from the information you are probably already receiving from the smart grid and providing you with a far more refined and focused assessment of your current threat level and changes in that threat level. By integrating this information with your SIEM, you can embed an appreciation of the low-voltage smart grid threat level into the wider context to protect yourself from multi-vector attacks.
With Grid Watch, you have added threat detection and response to complement your protection mechanisms, and you can now start looking at how to respond to the inevitable successful attack on your defences.
Protect. Detect. Respond!