How to Address Cybersecurity Vulnerabilities in the Low-Voltage Grid
In their recent paper, The energy-sector threat: How to address cybersecurity vulnerabilities 1, McKinsey and Company make compelling points about the vulnerability of utilities to cyber-attack:
• the increased awareness cyber-criminals have of the disruption that they can cause and the revenue they can generate
• the operational and geographical distribution of the utility and its impact on its ability to protect and react in a coherent manner
• the complexity of the energy supply-chain and the convergence of the physical and cyber components within it leading to the opportunity to do major damage by attacking relatively few points.
The paper outlines three main areas where utilities can apply their cybersecurity efforts and reduce their vulnerability:
• strategic intelligence on threats and actors before attacks on the network
• programs to reduce geographic and operational gaps in awareness and communication, creating a culture of security
• industry-wide collaboration to address the increasing convergence of physical and virtual threats.
The paper also outlines organisational structures and approaches to provide renewed cybersecurity. The approach centres on the establishment of SIEM/SOC infrastructure within utilities to anticipate and respond to threat and attack, improve communications and processes across geographic and operational boundaries and provide a source of threat awareness for industry-wide collaboration.
Your Low Voltage Smart Grid is a tempting target
Whilst these best-practices of ICT cybersecurity can be effectively deployed across the technology stack of a utility company as highlighted in the McKinsey and Company paper, the low-voltage grid deserves a special attention. In this part of the energy grid, intelligence is being introduced at a rapid rate, and all the vulnerabilities of utilities identified in the report are particularly relevant here.
The convergence of physical and cyber, a theme highlighted in the McKinsey paper, is particularly strong in the low-voltage grid, and is embodied in the Smart Meters that are being deployed in tens of millions around the world. The Smart Meter is no longer synonymous with just billing – it is a sensor and an interconnected control point in the energy supply-chain – an attack on the Smart Meter can significantly disrupt the energy supply and utility back-end operations - far beyond the relatively minor impact to bill processing.
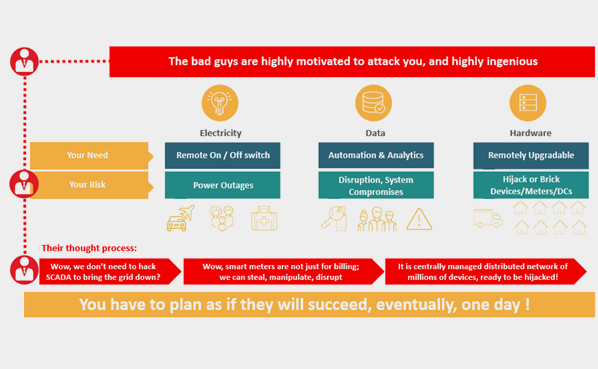
The methods that cyber criminals use to test and attack the Smart Meter are specific to these devices; their technology, the topologies they implement and the operational processes to deploy, maintain, update, and replace them. Applying generalised best practices to utilities provides the framework for establishing effective cybersecurity, but the differences between Smart Meters and generic ICT appliances lead to fairly different approaches for cybersecurity in the low-voltage grid.
The McKinsey and Company report places focus on airgaps between components of the IT and OT to offer protection should one part of the infrastructure be penetrated. Whilst this is a key form of protection, it is complemented by systems designed to assume that the protection is breached despite airgaps (and similar preventative solutions). A comprehensive cybersecurity solution must do all it can to prevent attacks, but ultimately, assume a breach will happen.
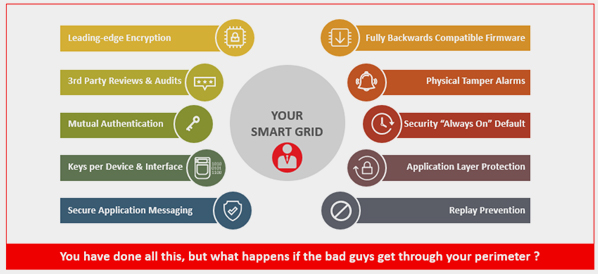
Is your Smart Grid really secure? Is protection enough by itself?
NES Grid Watch has been developed to both align to the overall cybersecurity organisation and strategy described in the McKinsey and Company paper and, also, to provide out-of-the-box capabilities specific to the low-voltage grid and the Smart Meters. Looking at each of the cybersecurity objectives defined by the McKinsey paper:
| Low-Voltage Grid Specifics | NES Grid Watch Response | Detection | |
| Strategic intelligence on threats and actors before attacks on the network | Specific threats and actors in the low-voltage grid are dependent on the technology, topology and operational processes deployed and executed on the Smart Meters and other smart devices | Embeds analytics derived from results of practical “ethical hacking” of such infrastructure to ensure that threats and actors are anticipated and that strategic intelligence is built into and maintained within the application | Embed an understanding of how the Smart Meters and other smart devices will indicate breach of the protection layer, and use this to define the scope and probable intent of a reconnaissance and actual attack |
| Programs to reduce geographic and operational gaps in awareness and communication, creating a culture of security | The practical reality is multiple versions of Smart Meter and smart devices, multiple vendors, multiple firmware, and multiple configurations. A wide range of geographic and operational gaps are inevitable and can only be partly addressed through organisation | Assumes a breach due to the highly heterogeneous and interconnected nature of the low-voltage grid, and integrates into the corporate SIEM to provide security indicators specific to the low-voltage grid | Breach is inevitable, and rapid exposure into a SIEM allows the SOC to understand the wider threat landscape, especially if this is multi-vector threat, as has been experienced in the more sophisticated cyber attacks |
| Industry-wide collaboration to address the increasing convergence of physical and virtual threats | Methods of attack are highly specific to the low-voltage grid. Generalised ICT cybersecurity best practices do not reflect the specific technologies, topologies and operational processes which will be exploited by the attacker of the low-voltage grid | The next versions of Grid Watch will share anonymised information about threats and attacks across the community of Grid Watch users, allowing them to brace for attack, knowing the specifics of the low-voltage grid attacks that are being mounted elsewhere | Detecting those attacks which are becoming more popular amongst cyber criminals and sharing the information will help utilities prepare themselves for attacks and implement the means to detect them when they are taking place |
NES Grid Watch is a practical solution for low-voltage cybersecurity threat detection, that can be integrated into a strategic SIEM and SOC that fully extends the activities of any utility implementing the framework set out in the McKinsey and Company paper.